Gitleaks is an open-source SAST tool designed to help identify sensitive information (such as passwords, API keys, and other secrets) accidentally exposed in a Git repository. It scans the entire commit history of a repository to detect and prevent secrets from being leaked or unintentionally stored within the repository’s codebase.
When developers or teams work on projects, they might unknowingly commit or push code that includes these sensitive details. Gitleaks aims to identify and alert individuals to such leaks, helping to prevent security breaches and maintain the confidentiality of the information stored in repositories.
It works by examining the commit history and contents of a Git repository, searching for patterns that resemble common forms of sensitive information. It uses regular expressions and configurable rules to recognize patterns that may indicate the presence of sensitive data.
Developers and security teams use Gitleaks as a preventive measure to avoid unintentional exposure of sensitive information in their codebase. Regular scans with Gitleaks can help in identifying potential security risks and prompt necessary actions to secure the codebase by removing or safeguarding sensitive data.
By providing a quick and automated way to scan Git repositories for leaks, Gitleaks assists in ensuring the security and integrity of the codebase and helps in maintaining best practices for handling sensitive information within a development environment.
Before you can use Gitleaks, you will need to install it. To install Gitleaks, you have several options depending on your operating system. Here are some of the common methods:
Using Package Managers
1. Homebrew (for macOS):
If you’re using macOS, you can install Gitleaks using Homebrew.
Open a terminal and run the following command:
brew install gitleaks2. Scoop (for Windows):
If you’re using Windows and have Scoop installed, you can install Gitleaks via Scoop.
Open a PowerShell or Command Prompt and run the following command:
scoop install gitleaksDownload Pre-built Binary
Download the binary from the Releases page:
- Visit the Gitleaks GitHub Releases page.
- Download the appropriate binary for your operating system (e.g., gitleaks-Darwin-x64 or gitleaks-Linux-x64).
- Extract the downloaded file and place the executable in a directory within your system’s PATH for easy access.
Building from Source
Clone and build from the repository:
- Clone the Gitleaks repository from GitHub using Git.
- Navigate to the cloned directory.
- Run the build command to compile the source code.
git clone https://github.com/gitleaks/gitleaks.git
cd gitleaks
make buildHow to use Gitleaks?
Gitleaks proves valuable in various situations, and I’ve outlined the most prevalent scenarios below:
Use Case 1:
I’ve committed all changes in my Git source code repository and now I’m seeking to discover whether any secrets have been included in the commits.
Execute the provided command to check for any committed secrets in your Git repository.
gitleaks detect .Execute the following command to retrieve details about the secrets that have been committed to your Git repository.
gitleaks detect -v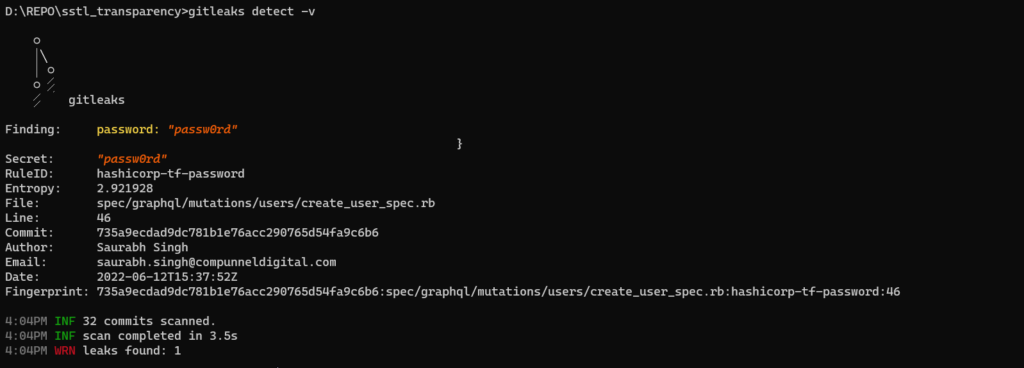
Use Case 2:
I want to ensure that I avoid committing any secrets to my Git source code repository.
Execute the provided command to find any secrets in your code changes
gitleaks protect .Execute the following command to retrieve details about the secrets in your code
gitleaks protect -vGitleaks Usage
Usage:
gitleaks [command]
Available Commands:
completion generate the autocompletion script for the specified shell
detect detect secrets in code
help Help about any command
protect protect secrets in code
version display gitleaks version
Flags:
-b, --baseline-path string path to baseline with issues that can be ignored
-c, --config string config file path
order of precedence:
1. --config/-c
2. env var GITLEAKS_CONFIG
3. (--source/-s)/.gitleaks.toml
If none of the three options are used, then gitleaks will use the default config
--exit-code int exit code when leaks have been encountered (default 1)
-h, --help help for gitleaks
-l, --log-level string log level (trace, debug, info, warn, error, fatal) (default "info")
--max-target-megabytes int files larger than this will be skipped
--no-color turn off color for verbose output
--no-banner suppress banner
--redact redact secrets from logs and stdout
-f, --report-format string output format (json, csv, junit, sarif) (default "json")
-r, --report-path string report file
-s, --source string path to source (default ".")
-v, --verbose show verbose output from scan
Use "gitleaks [command] --help" for more information about a command.GitLeaks is a robust tool designed to enhance the security of your code repository by notifying you of any inadvertent inclusion of sensitive information. By installing and setting up GitLeaks, you can guarantee the security of your codebase and stay informed about the presence of any sensitive information.