In this blog, I will walk you through the process of securing your Terraform code, proactively identifying and mitigating potential vulnerabilities, and ensuring the protection of your infrastructure access.
With the rising popularity of Infrastructure as Code (IaC), tools like Terraform have become indispensable for organizations, ranging from startups to large enterprises, to manage their infrastructure programmatically. However, challenges such as security and quality remain critical concerns that demand attention, don’t they?
Numerous policy-as-code tools are accessible in the market, including Snyk, Checkov, Terrascan, Aqua-TFSec, and others. Today, I’ll focus on Checkov in conjunction with Terraform, exploring its capabilities in identifying compliance and security breaches.
What is Checkov?
Checkov is an open-source static code analysis tool designed specifically for infrastructure as code (IaC) frameworks like Terraform, Kubernetes YAML, AWS CloudFormation, and others. It scans your IaC scripts to identify misconfigurations, security vulnerabilities, and compliance violations against best practices and industry standards. Checkov helps ensure that your infrastructure deployments are secure, compliant, and resilient by providing actionable insights and recommendations for remediation.
How to set up Checkov?
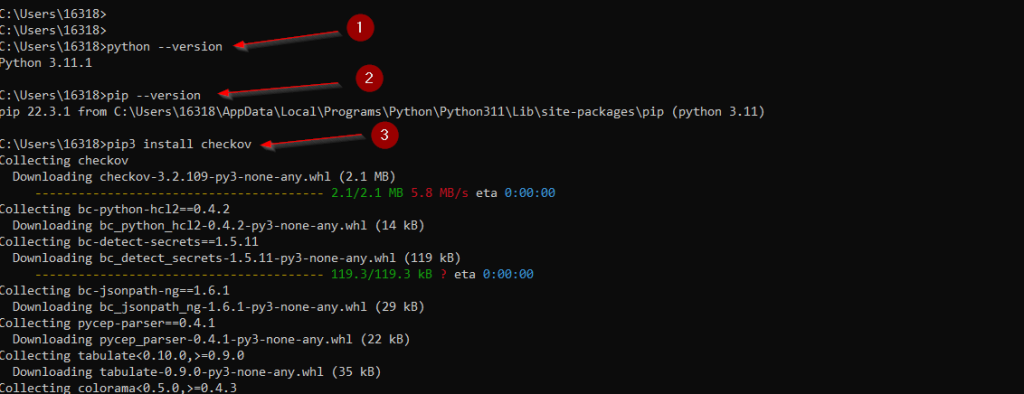
To install Checkov, you can use pip, the package installer for Python. Here’s a step-by-step guide:
- Ensure Python and pip are installed:
- Check if Python is installed:
python --version - Check if pip is installed:
pip --version
- Check if Python is installed:
- Install Checkov using pip:
- Open your terminal or command prompt and run the following command:
pip3 install checkov - Verify the installation:
checkov --version
- Open your terminal or command prompt and run the following command:
Scan the Terraform Project Plan
Let’s consider a scenario where your project requires an S3 bucket configured according to AWS best practices.
Our initial version of main.tf will look like this:
provider "aws" {
region = "us-east-1"
}
resource "aws_s3_bucket" "cloudcuddler_bucket" {
bucket = "cloudcuddler-bucket"
tags = {
Name = "cloudcuddler"
}
}Initalize the terraform code:
terraform initconvert the tf.plan file to JSON format:
terraform plan -out=tfplan -input=false
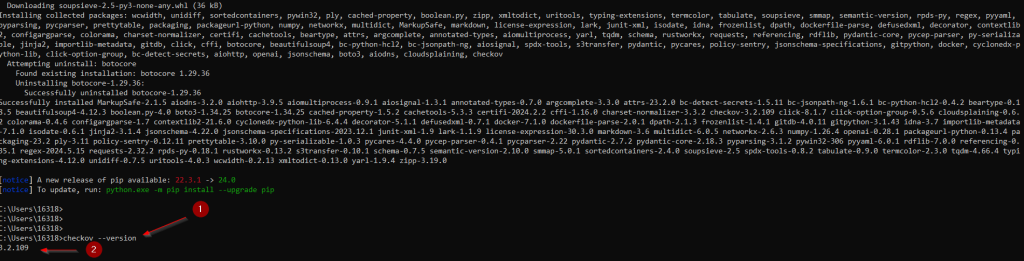
terraform show -json tfplan > tfplan.jsonNow, scan the terraform tf.json file:
checkov -f tfplan.jsonCheckov Report
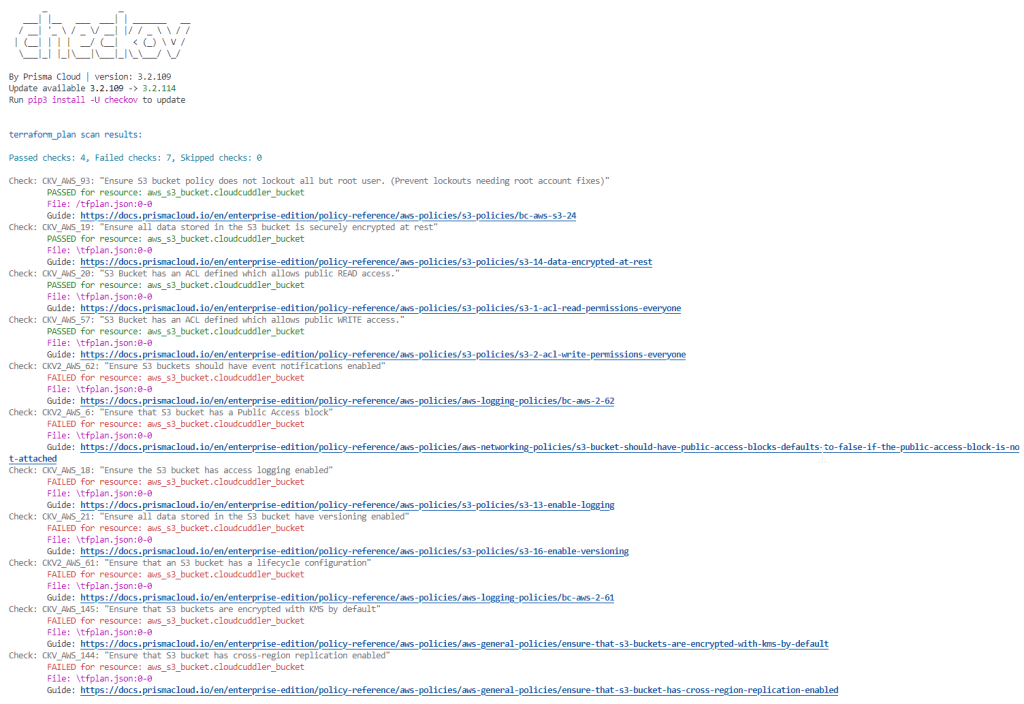
To address the failed checks, follow the guidance provided in the output for each respective failed check. Once all checks have passed, review the Terraform plan for the configuration and then proceed to apply it.
Official Website - www.checkov.io
CLI Command Referce - Click Here
Checkov Custom Policy - Click Here
Integrate Checkov with Jenkins - Click Here
I recommend incorporating Checkov into your IaC code development process to mitigate risks and enhance compliance.