In the preceding section, I explored the organizational framework of AWS, delving into its principles and significant advantages. Within this structure, I outlined four accounts within the Core Organization Units: the Security Account, Log Archive Account, Network Account, and Shared Service Account. The forthcoming discussion in this blog will center on these four Core accounts, along with insights into the master account.
Master Account
In AWS Organizations, the term “master account” refers to an AWS account to create the organization. The master account in the AWS organization is unique. We also refer to it as the organization management account or org management account.
When you set up an AWS organization, you designate one of your existing AWS accounts as the master account. This master account gains certain administrative privileges and controls over the entire organization, allowing it to manage policies, create and invite other member accounts, and consolidate billing information.
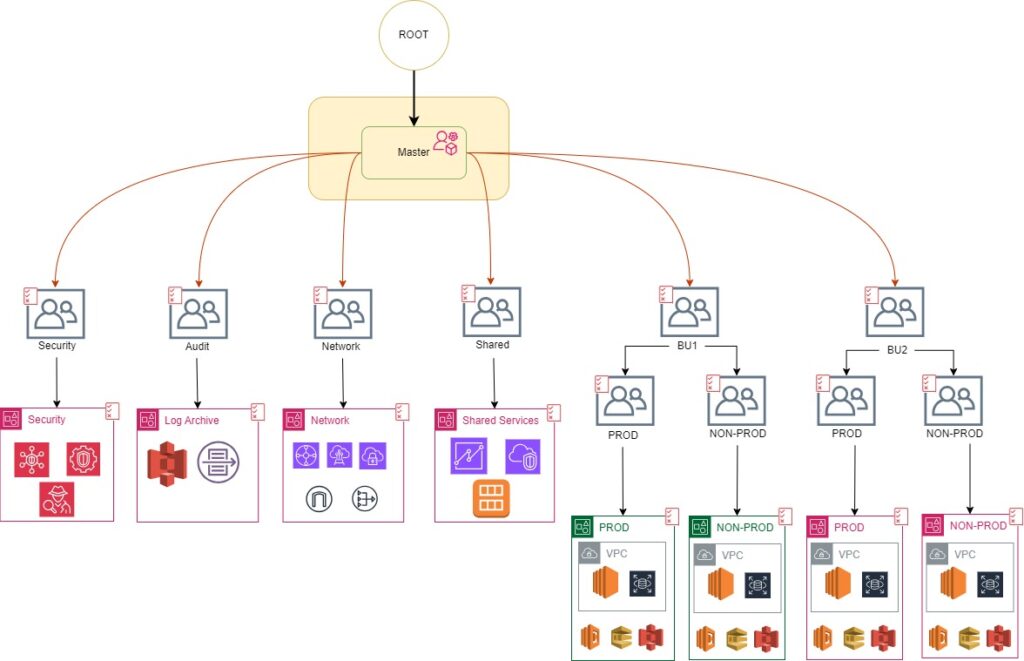
Key characteristics and responsibilities of the master account in an AWS organization:
-
Creating the Organization: The master account is responsible for initiating the creation of the AWS organization.
-
Inviting Member Accounts: It can invite other AWS accounts to join the organization as member accounts.
-
Setting Policies: The master account has the authority to define and apply organizational policies that affect all member accounts. These policies may include service control policies (SCPs) that limit the services and actions available to member accounts.
-
Billing Consolidation: The master account is the focal point for consolidated billing, meaning it receives and pays the bills for all accounts within the organization. This simplifies the billing process for multiple accounts by aggregating charges into a single payment.
-
Access to AWS Organizations Console: The master account has access to the AWS Organizations console, which provides a centralized interface for managing and monitoring the organization’s structure and policies.
It’s important to note that while the master account has elevated administrative capabilities, it doesn’t automatically have access to the resources of member accounts. Permissions for specific resources within member accounts are managed separately through Identity and Access Management (IAM) policies.
In summary, the AWS master account plays a central role in the management and coordination of an AWS organization, with a focus on administrative tasks, policy enforcement, and consolidated billing.
Security Account
The AWS Security Account actively manages security-related functions and services across the entire landing zone. This dedicated account centralizes management by receiving status updates and data from other accounts within the organization, enabling unified control.
Key aspects of the AWS Security Account within the AWS Landing Zone
-
Centralized Security Management: The Security Account in AWS Landing Zone serves as a centralized hub for managing security-related configurations, services, and controls across the entire Landing Zone environment.
-
Security Services Hosting: This account often hosts critical security services such as AWS Security Hub, AWS GuardDuty, and AWS Config. These services provide comprehensive security monitoring, threat detection, and compliance checks for the entire Landing Zone.
-
Cross-Account Access: The Security Account is granted cross-account access to other AWS accounts within the Landing Zone. This allows it to enforce security policies consistently across all accounts and implement security configurations uniformly.
-
Logging and Monitoring: The Security Account is responsible for centralizing logs and monitoring data from various AWS accounts within the Landing Zone. Services like AWS CloudTrail and AWS CloudWatch may be configured to provide audit trails and monitoring capabilities.
-
Incident Response: In the event of a security incident, the Security Account may play a role in incident response activities.
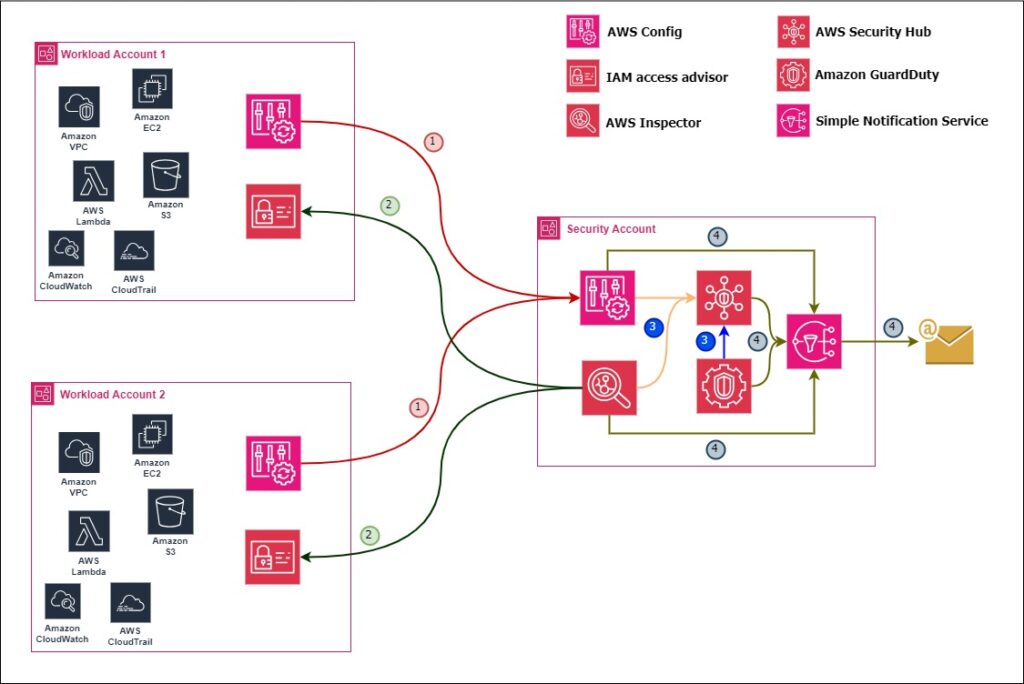
Legend as per the above design document
AWS Config 1 is indeed a service provided by Amazon Web Services (AWS) that allows users to assess, audit, and evaluate the configurations of their AWS resources. Its primary purpose is to help users maintain an accurate and up-to-date inventory of their AWS resources, track changes over time, and gain insights into the historical configuration states.
-
Configuration Assessment
-
Compliance Management
-
Audit and Security Analysis
-
Change Management
-
Operational Troubleshooting
AWS Inspector 2 is indeed an automated security assessment service provided by Amazon Web Services (AWS). AWS Inspector is designed to perform continuous security assessments by scanning Amazon EC2 instances and container workloads for potential vulnerabilities and unintended network exposure.
-
Automated Vulnerability Management
-
Continuous Scanning
-
EC2 and Container Workload Coverage
-
Identification of Security Issues
-
Integration with Other AWS Services
-
Security Compliance Assessments
Security Hub 3 is a cloud security posture management service that performs security best practices checks, aggregates alerts, and enables automated remediation. Using the Security Hub, you can aggregate findings from various security services such as AWS Config, GuardDuty, Amazon Macie, AWS Inspector, etc
-
Cloud Security Posture Management (CSPM)
-
Alert Aggregation
-
Security Best Practices Checks
-
Compliance Standards
-
Integration with AWS and Third-Party Tools
-
Automated Remediation
-
Prioritization and Insights
4 – Notification 4 Using AWS Simple Notification Service, Security engineers can get notifications in case of any security issue.
Network Account
In an AWS Landing Zone, the network account is a dedicated account within a multi-account structure designed for managing and controlling networking infrastructure. This approach adheres to best practices for organizing resources, enhancing security, and enabling scalability.
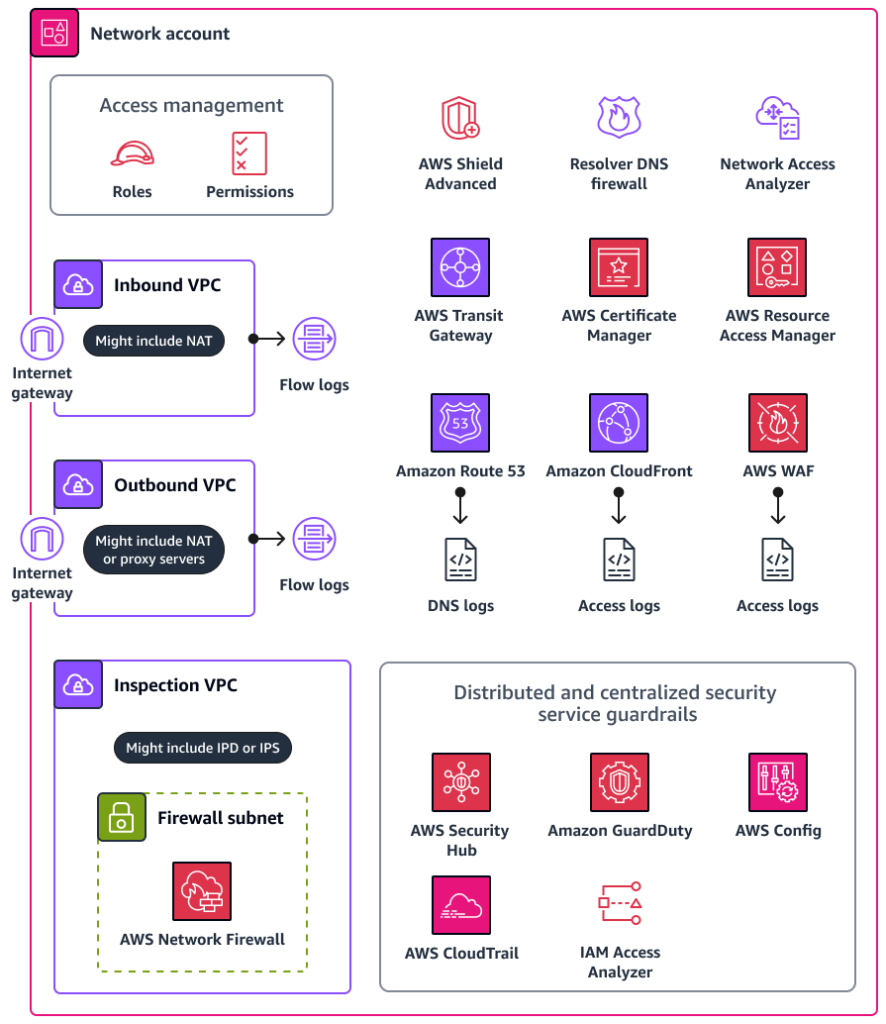
Key Components of a Network Account in an AWS Landing Zone
Centralized Networking:
- Acts as a hub for managing VPCs, routing, and connectivity between AWS accounts in the landing zone.
- Implements shared services like a Transit Gateway or AWS Direct Connect for hybrid cloud setups.
Shared VPCs:
- Hosts shared VPCs that other accounts can utilize through VPC sharing.
- Helps reduce duplication of VPCs while maintaining centralized control over networking resources.
Connectivity Services:
- VPN Connections: Configured for secure access to on-premises environments.
- Direct Connect: Manages high-speed, low-latency connections to on-premises networks.
- AWS Transit Gateway: Facilitates inter-VPC communication and acts as a centralized hub for routing.
Security and Compliance:
- Centralized management of security groups, network ACLs, and other access controls.
- Integration with AWS Firewall Manager to enforce security policies across multiple accounts.
Peering and Routing:
- Handles VPC peering between accounts.
- Manages route tables and ensures efficient traffic flow between resources.
DNS and IP Management:
- Coordinates IP address management (IPAM) to avoid conflicts across accounts.
- Centralizes the use of Route 53 for DNS management.
Log Archive Account
The Log Archive Account is a critical part of an AWS Landing Zone architecture. It serves as a centralized repository for storing and managing logs across all AWS accounts within the landing zone. Centralizing log data in a dedicated account enhances security, auditability, and compliance.
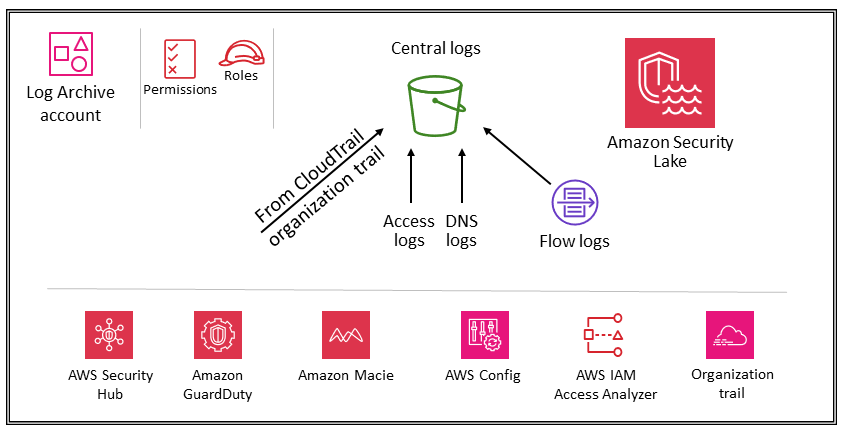
Key Responsibilities of a Log Archive Account
- Centralized Logging Repository – Collects logs from various AWS services across all accounts in the landing zone.
- Common log types include – AWS CloudTrail logs, Amazon VPC Flow Logs, AWS Config logs, Application and system logs
- Immutable Log Storage – Logs are stored in Amazon S3 buckets with strong access controls and configured lifecycle policies. Versioning and MFA Delete can be enabled to ensure log integrity and prevent accidental or malicious deletion.
- Access and Permissions – Implements fine-grained permissions to restrict access to logs, ensuring only authorized users or services can read or modify them. Cross-account IAM roles or Resource-Based Policies allow accounts to write logs to the Log Archive Account.






