Hello Techies,
Recently, I have started the preparation for AWS Certified Advanced Networking—Specialty, and during this, I thought I would like to share my learning path with all my friends who want to learn and understand AWS networking.
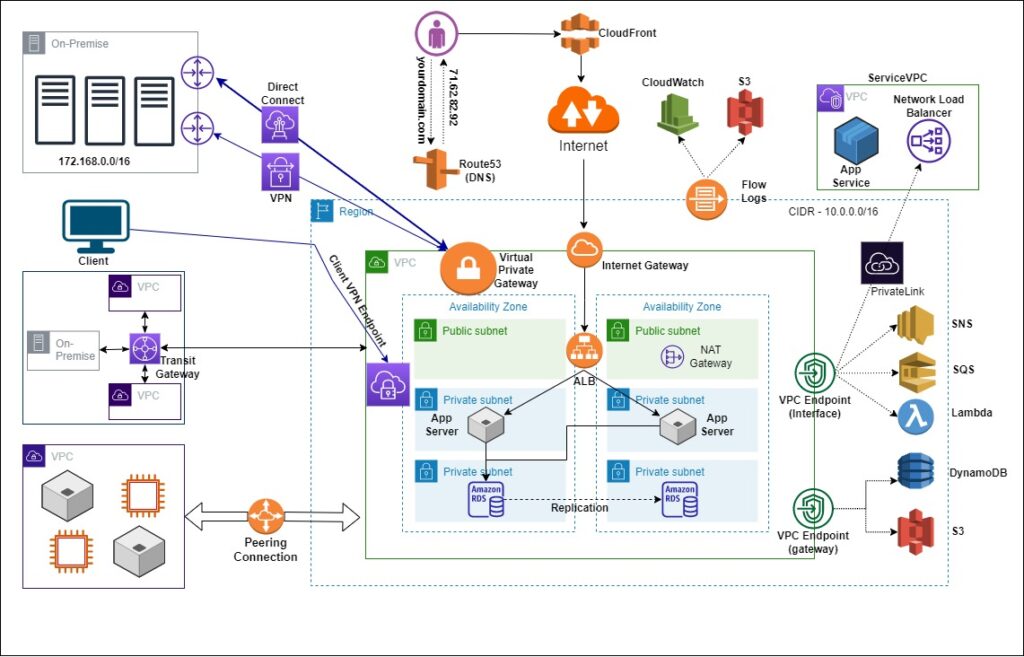
This is my first post in this networking concept, and I am sharing the architecture diagram for all AWS networking services and their uses.
In this article, I’m going to give you the details of all AWS networking services and put them in one architecture diagram, which will give you a bigger picture of AWS networking. This will help you understand when and where to use the network services.
Lets begin,
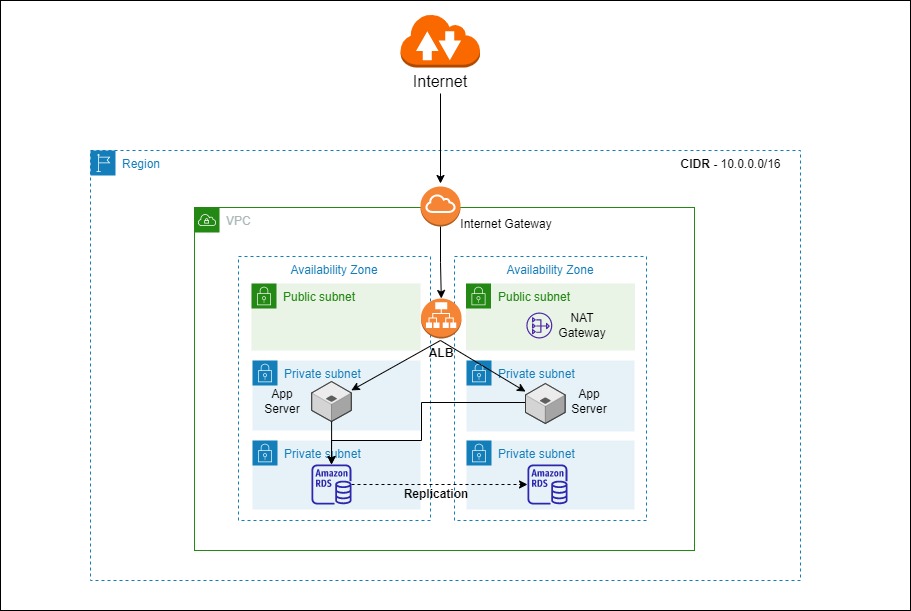
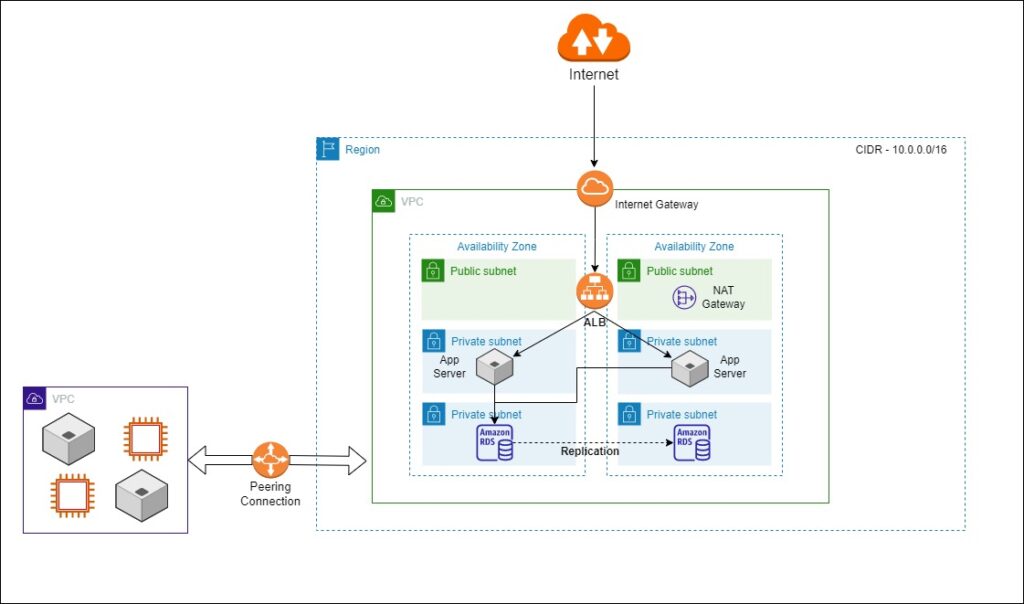
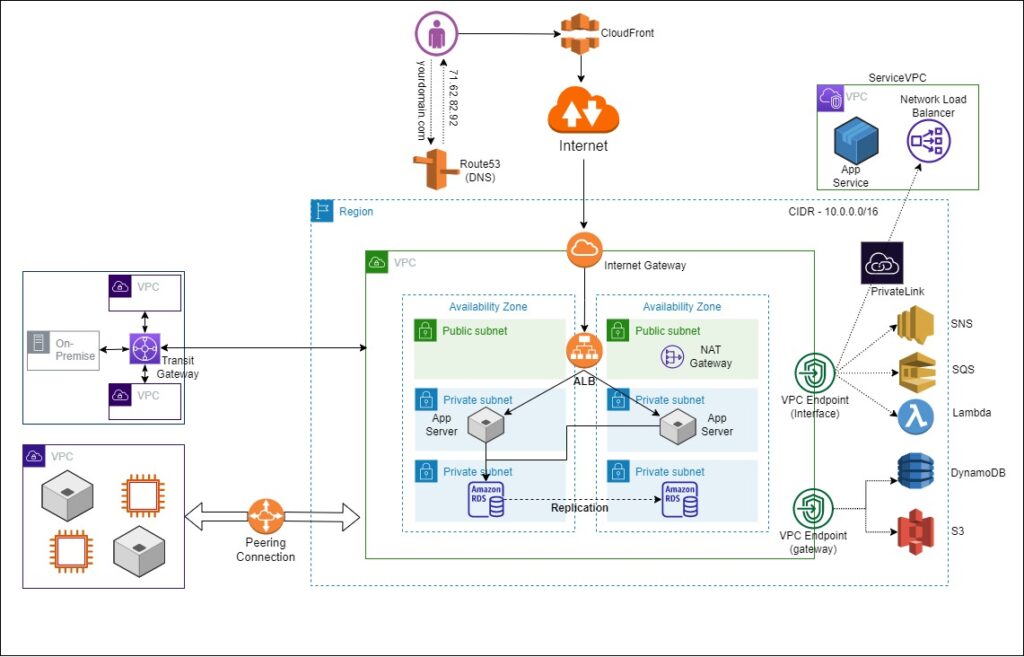
Base Network with 3-Tier Architecture
If you want to provision your network inside AWS, the starting point is to create a base network that includes a region, VPC, availability zone, subnets, internet gateway, NAT gateway, and application load balancer. 3-Tier Architecture Diagram, as mentioned
VPC Peering Connection
In the Base Network with 3-Tier Architecture, we can see that the application is running fine in your VPC. Assume that your customer says, “I want to access your VPC application without going over the internet.” In that case, you need to provide a private connection between the customer machine and your machines inside your VPC. For this, AWS provides a service called VPC peering connections. All traffic from the VPC peering flows through the AWS managed network, which improves network consistency and reliability.
Transit Gateway
In case your customer has multiple VPCs and has to connect these VPCs to on-premises networks as well. We can configure this by using the AWS networking router, which is called a transit gateway. The transit gateway allows you to connect different networks together, including the VPC as well as your on-premise network. So you can connect your on-premise network to the transit gateway using a VPN connection or a Direct Connect connection.
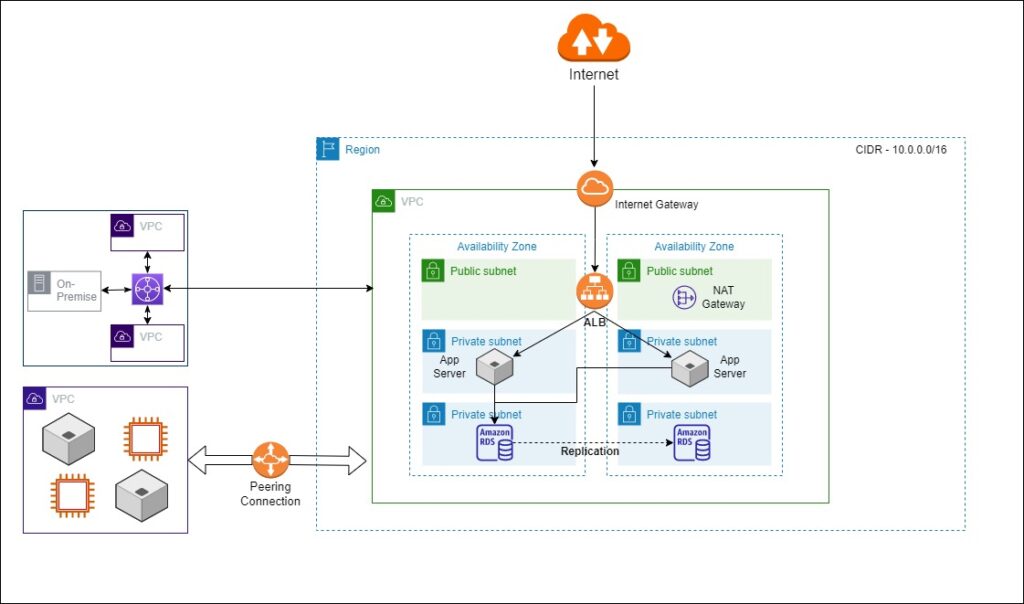
What is the difference between AWS Transit Gateway and VPC Peering?
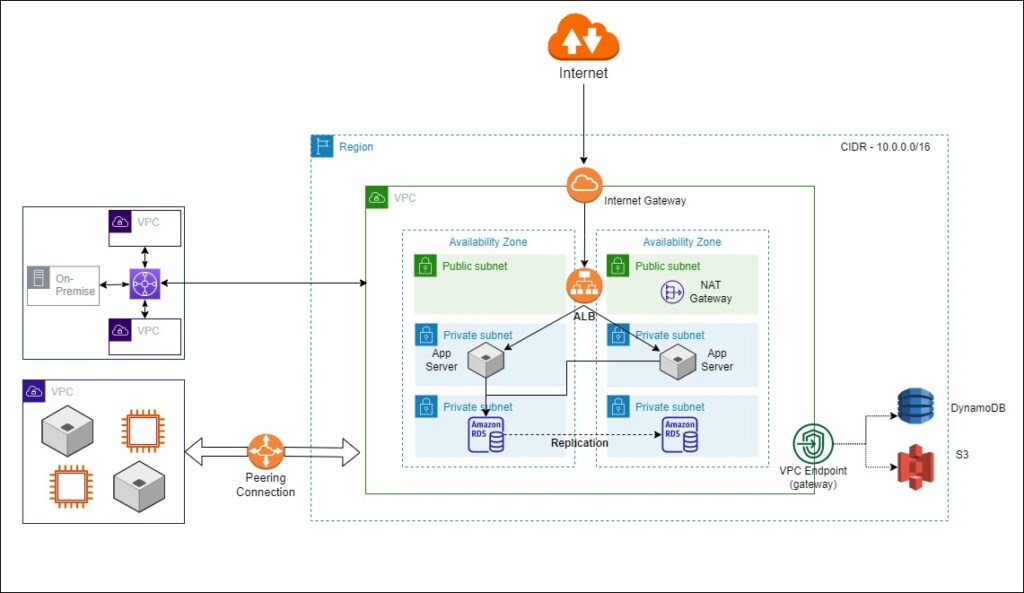
VPC Endpoint(gateway)
Most web applications need S3 storage to upload and download data. As you know, when you create an S3 bucket, you create it inside a region. If S3 and the application VPC are in the same region, then AWS recommends the VPC endpoint. The VPC endpoint allows you to access the S3 and DynamoDB services privately from your VPC. Now the condition is that the S3 and DynamoDB should be in the same region as your VPC.
VPC Endpoint(Interface)
Sometimes you want to connect to SQS queues or SNS, or you want to execute a Lambda function, or you want to make an API call for EC2 machines. Now these are also AWS services, and AWS provides a public endpoint for these services. But if you want to have private connectivity from your VPC to this API endpoint, then you can use the VPC endpoint interface.
If you want to connect to some AWS API endpoint, I would recommend first checking whether the VPC endpoint interface supports that endpoint or not.
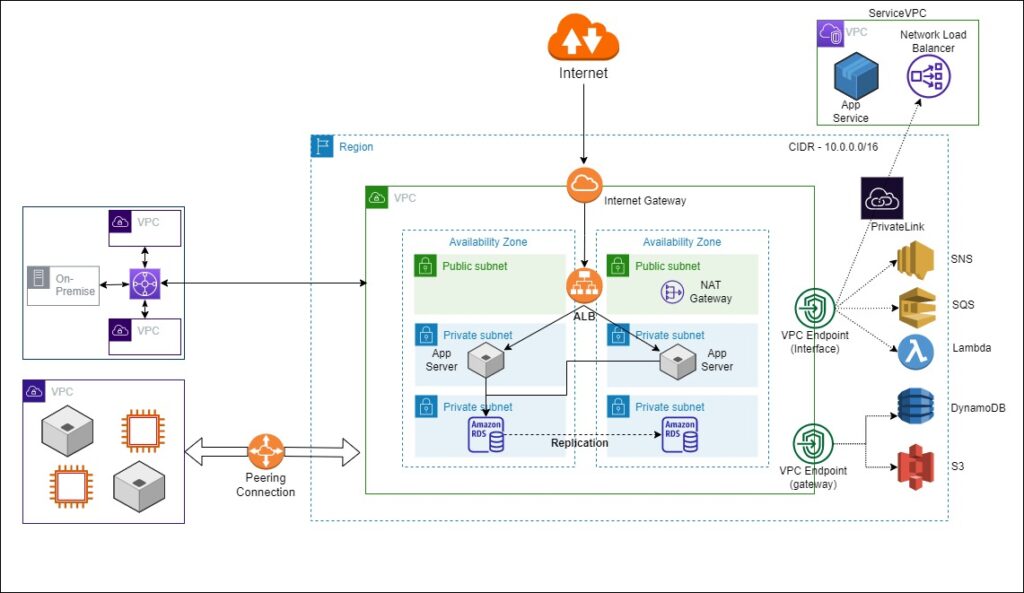
Let’s discuss here one addition to AWS networking components: Suppose your customer has one server, and they want to allow you to access their services privately from your VPC instead of exposing them over the internet.
Now for this, AWS has launched a networking service called a PrivateLink. Now, what PrivateLink means is that you expose your application services via the load balancer, and in a service consumer VPC, you create a VPC endpoint, and this endpoint will privately connect you to the network load balancer of the service provider VPC. And now this connection from this VPC endpoint to the network load balancer is private; it doesn’t go over the internet. And this is how you can now provide your services privately to as many customers as you want.
Route53 & CloudFront
In general, you want to use a DNS instead of an IP address. For this, you can use an AWS service, i.e., Route 53. So if the end user uses the domain name, e.g., yourdomain.com, for accessing the application and you have a Route 53 hosted zone for yourdomain.com, the query will go to the Route 53 and it will respond with the IP address of your web server. In this architecture, the load balancer’s IP address will be dynamically assigned, and you will only receive one IP address for this load balancer.
Now, for better performance, you can also use the AWS CloudFront service, which is a CDN (Content Delivery Network).
CloudFront basically does two things:
- It can cache your static content at the nearest edge locations for the user.
- It also connects you to the AWS VPC over the dedicated network.
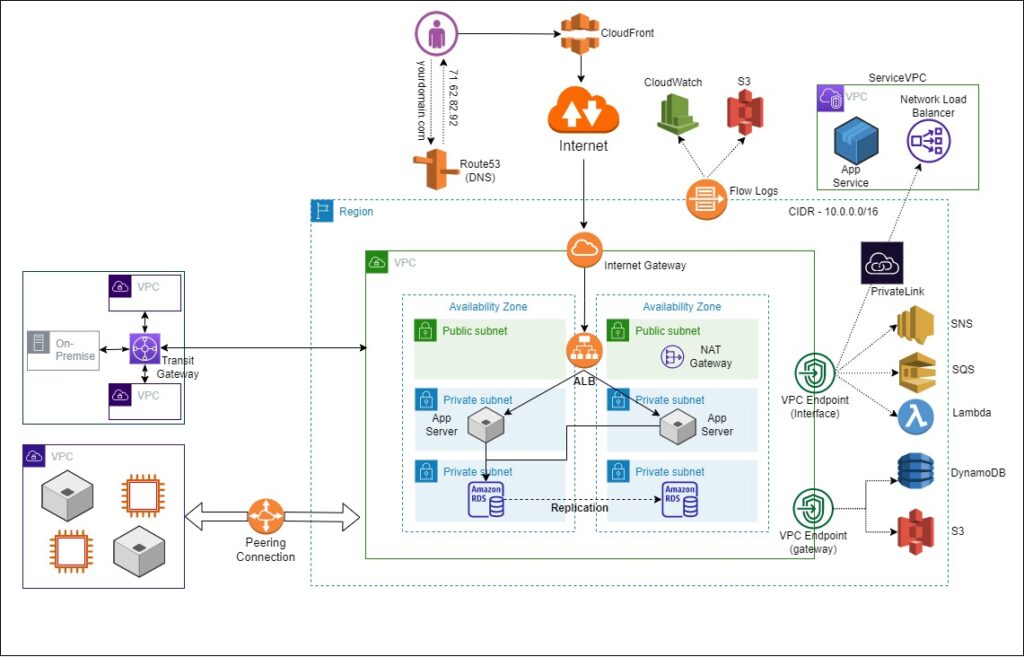
VPC Flow Logs
Audit and Troubleshooting: If you want to see all the packets flowing in and out of your VPC and capture those packets, you can enable the VPC flow logs, and these flow logs can then be dumped to CloudWatch or S3 for later analysis.
AWS Direct Connect & VPN
Now, in the case of hybrid mode, that means some of the workload might be running in the cloud and some of the workload might be running in the on-premise network. Then how do you connect your VPC to the on-premise data center? There are a couple of options provided by AWS.
- A very simple option is using the Site-to-Site VPN connection. You need to attach a Virtual Private Gateway to your VPC, and then using the VPG, you can establish an IPsec VPN with the on-premise router.
- The second option is client-to-site VPN.
- The third option is AWS Direct Connect, which is actually a physical connection from an AWS VPC to your corporate data center.