Kubernetes namespaces provide logical separation and organization within a cluster. However, improper usage can lead to mismanagement, resource conflicts, and security risks. Here are some common mistakes and practical tips to avoid them.
1. Overlooking Resource Quotas
Mistake: Not defining resource quotas in namespaces can cause resource
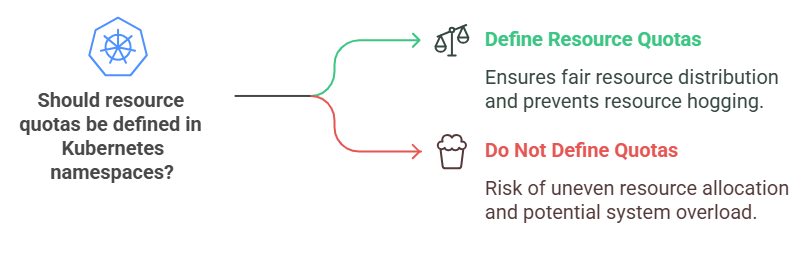
Solution: Always define resource quotas to control CPU, memory, and pod count per namespace.
apiVersion: v1
kind: ResourceQuota
metadata:
name: production-quota
namespace: production
spec:
hard:
requests.cpu: "4"
requests.memory: 8Gi
limits.cpu: "8"
limits.memory: 16GiWhen managing Kubernetes namespaces, it’s crucial to define resource quotas clearly and explicitly. Resource quotas help you control the maximum amount of CPU, memory, and number of pods each namespace can use. Without these quotas, one namespace might unexpectedly consume excessive resources, causing performance degradation or resource shortages for other namespaces within the cluster. Implementing resource quotas ensures fair resource distribution, prevents over-consumption, and helps maintain stable, predictable cluster operations.
2. Ignoring Namespace Isolation
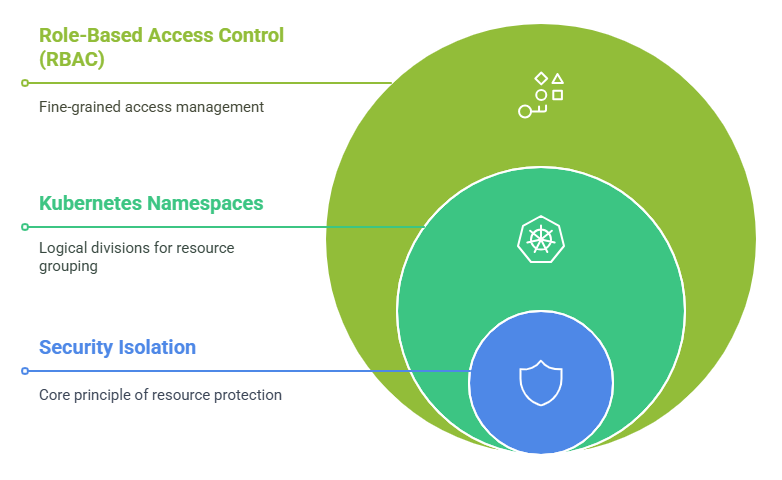
Mistake: Assuming namespaces inherently provide security isolation.
Solution: Implement Role-Based Access Control (RBAC) to ensure secure isolation.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: dev
name: dev-role
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "create"]Role-Based Access Control (RBAC) is essential in Kubernetes namespaces for securing resources. RBAC enables precise control over who can access specific resources and what actions they can perform. Implementing RBAC within namespaces ensures that users and applications can only interact with permitted resources, significantly enhancing security by preventing unauthorized access and accidental modifications.
3. Poor Namespace Naming Conventions
Mistake: Using unclear or inconsistent namespace names, causing confusion.
Solution: Adopt a clear, descriptive, and consistent naming convention, such as:
- Environment-based:
prod,dev,staging - Team-based:
frontend-team,backend-team

4. Mixing Environment Workloads
Mistake: Running development and production workloads in the same namespace.
Solution: Always segregate environments into distinct namespaces, enhancing security, stability, and troubleshooting.
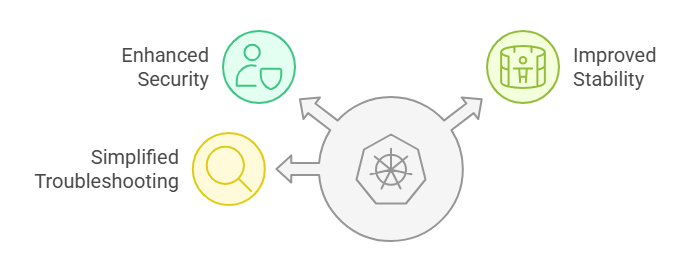
It’s crucial to run your development, staging, and production workloads in separate Kubernetes namespaces. Mixing these environments within a single namespace can create security vulnerabilities, make resource management challenging, and complicate troubleshooting. Segregating workloads into distinct namespaces enhances clarity, provides secure boundaries, simplifies issue diagnosis, and ensures stable and predictable cluster operations.
5. Forgetting LimitRange Policies
Mistake: Not defining resource limits per pod/container, leading to unpredictable resource consumption.
Solution: Define LimitRange policies within namespaces to enforce minimum and maximum resource usage.

apiVersion: v1
kind: LimitRange
metadata:
name: resource-limits
namespace: testing
spec:
limits:
- default:
cpu: "500m"
memory: "512Mi"
defaultRequest:
cpu: "250m"
memory: "256Mi"
type: ContainerLimitRange policies in Kubernetes namespaces help manage resource usage effectively by setting clear boundaries for resource consumption per pod or container. Without LimitRanges, pods or containers might consume unpredictable amounts of CPU or memory, leading to potential resource shortages and performance issues. Defining LimitRanges ensures each resource operates within expected limits, maintaining stability and predictability across your Kubernetes clusters.
6. Not Cleaning Up Unused Namespaces
Mistake: Leaving unused namespaces active, consuming resources unnecessarily.
Solution: Regularly review and clean up unused namespaces and resources using automated scripts or scheduled jobs.
kubectl delete namespace <unused-namespace>7. Lack of Monitoring at the Namespace Level
Mistake: Monitoring cluster resources without granularity, leading to unnoticed resource bottlenecks.
Solution: To gain precise insights, implement namespace-level monitoring using tools like Prometheus, Grafana, or a Kubernetes-native metrics server.
Avoiding these common mistakes can significantly improve Kubernetes cluster management, enhancing security, performance, and maintainability. By following best practices and utilizing Kubernetes features like resource quotas, RBAC, and proper monitoring, you ensure a smoother, safer, and more efficient Kubernetes operation.